Google launches Key Transparency tool to confirm the cryptokeys
Reliable cryptography is the basis of the modern Internet. Without cryptography there is no a secure connection, you lose the possibility of making a reliable transaction online. We can't even trust the interlocutor if you do not have a secure connection.
According to Google, the current infrastructure of public cryptography, there is a serious flaw. The fact that in case of compromised server keys users have to manually check the interlocutor. This is extremely inconvenient and does not work in practice. Because of these difficulties, some enthusiasts of cryptography refuse to PGP, and they can be understood.
Google has come up with a solution: Google offers to all to use transparent mechanism of public keys the search is Key Transparency.
The problem is that the web of trust PGP to encrypt email was created more than 20 years ago, and many users still can't or don't want to use it.
Problem of PGP
The problem is well described by a specialist in cryptography Filippo in his article "I'M GIVING UP ON PGP":
I never ever ever successfully used the WoT to validate a public key. And remember I have a well linked key. I haven't done a formal study, but I'm almost positive that everyone that used PGP to contact me has or would have done (if asked) one of the following:
- pulled the best-looking key from a keyserver, most likely not even over TLS
- used a different key if replied with "this is my new key"
Travel in particular is hostile to long-term keys, making this kind of fresh start impractical.
- resent the email unencrypted if provided an excuse like "I'm traveling"
Moreover, I'm not even sure there's an attacker long term keys make sense against. Your average adversary probably can't MitM Twitter DMs (which means you can use them to exchange fingerprints opportunistically, while still protecting your privacy). The Mossad will do Mossad things to your machine, whatever key you use.
Finally, these days I think I care much more about forward secrecy, deniability and ephemerality than I do about iron clad trust. Are you sure you can protect that long-term key forever? Because when an attacker decides to target you and succeeds, it won't have access from that point forwards, but to all your past communications, too. And that's ever more relevant.
Many will agree with this opinion.
From the same problems with the key exchange suffer instant messengers, programs for file exchange and delivery system for software updates.
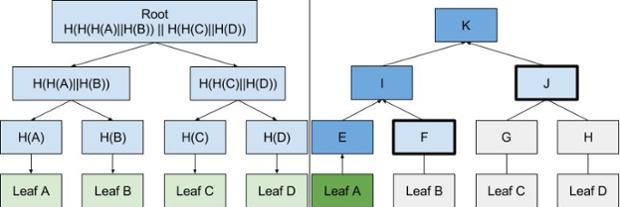
Key Transparency
Key Transparency — transparent public catalog through which developers will easily create any kind of system with an independently verifiable data of the accounts, It can be used in a variety of scenarios where data needs to be encrypted or authenticated. It can be used to develop user-friendly security features, at the same time, support important needs of the user, as the recovery account.
— Saud Ryan Hirst and Gary Belvin
According to the authors, the development of Key Transparency they have combined the properties of the Certificate Transparency and CONIKS.
Google's Certificate Transparency is an open framework for monitoring and auditing SSL certificates in near real time. If the certification authority by mistake or intentionally issued new SSL certificates, they will be quickly detected by the system Certificate Transparency. The system also determines if the CA issues fake certificates.
On the other hand, CONIKS is a key management system for end-users so that they can maintain secure channels end-to-end encryption even if the provider or server does not trust. That is CONIKS stores the encryption keys for the user in such a way that they are available for inspection and any replacement keys instantly fixed.